Kafka Cluster Onboarding Guide
This guide outlines the steps to onboard your Kafka cluster into the Axual Governance using its Wizard.
Prerequisites
-
Make sure that you have a running Axual Governance that you can access.
-
To make the onboarding Wizard visible, you need to configure your values.yaml with
skip-onboardingset to false for your Platform-Manager:
platform-manager:
config:
axual:
default:
skip-onboarding: false-
For the Kafka cluster, you are onboarding:
-
Connectivity information (endpoint, port)
-
Security information (certificates, SASL credentials)
-
Kafka and Schema Registry authentication
Depending on the type of authentication which is enabled on Kafka and Schema Registry, there are additional prerequisites. Check the prerequisites for your type of authentication below.
Kafka authentication
| Mutual TLS (mTLS) | SASL |
|---|---|
If you are using mutual TLS (mTLS) to authenticate to Kafka, there are additional prerequisites:
|
If you are using SASL to authenticate to Kafka, there are additional prerequisites:
|
Schema registry authentication
If you use authentication on the schema registry interface, you need some additional information:
| Basic authentication | TLS |
|---|---|
The username and password to authenticate to Schema Registry |
|
| Axual Governance only supports X.509 certificates in the PEM format and PKCS8 private keys in the PEM format. The extension of certificate and private key can be anything (for example .crt, .pem, .key, .p8 etc). |
Initial Setup: Organization Information
-
Log into the Self-Service interface via the following URL:
https://[governance-domain]/login/local. The following screen will be shown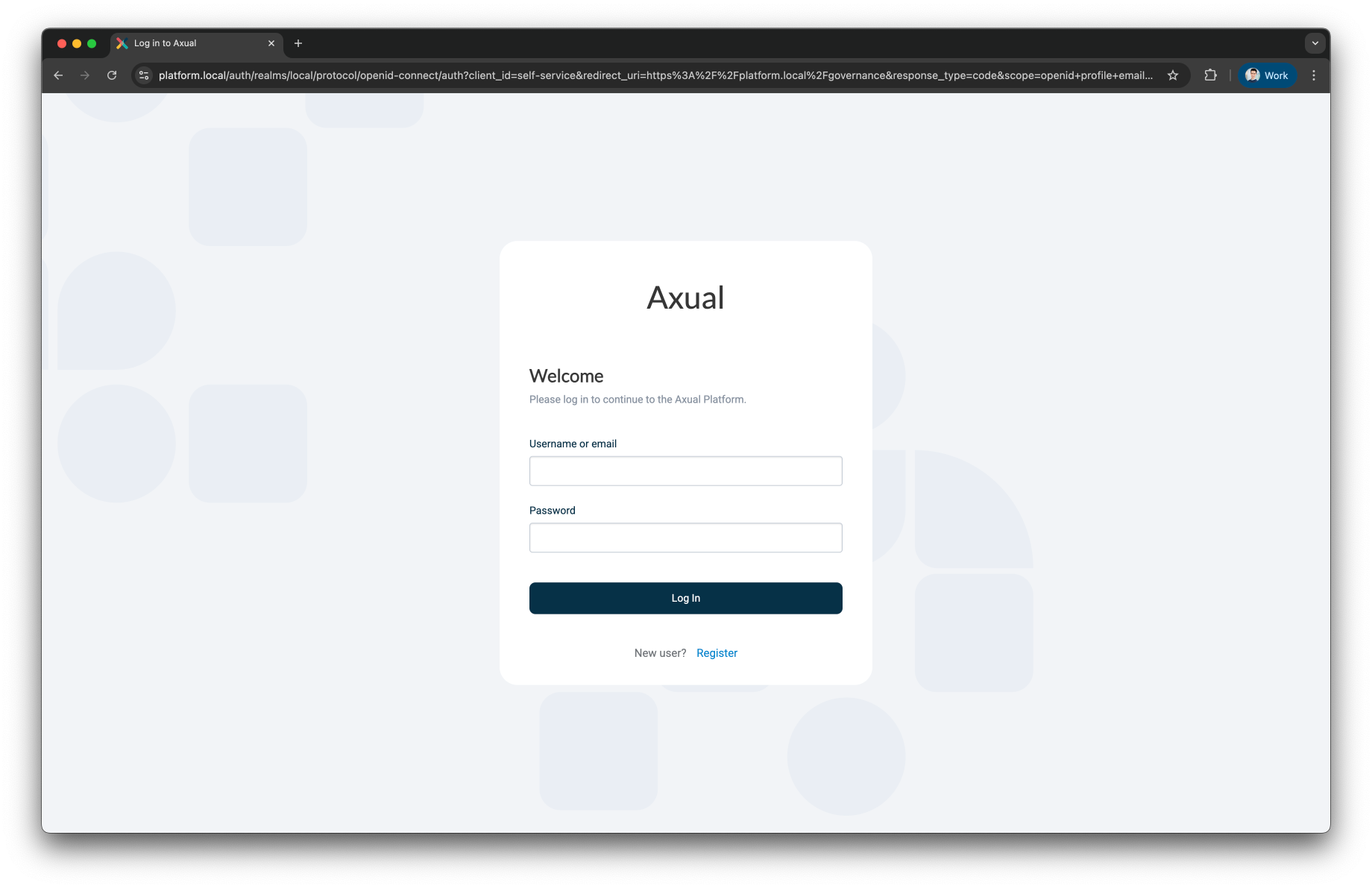
-
Click Register to register a Tenant Admin user. This user has administrative privileges on the platform. The following screen will be shown
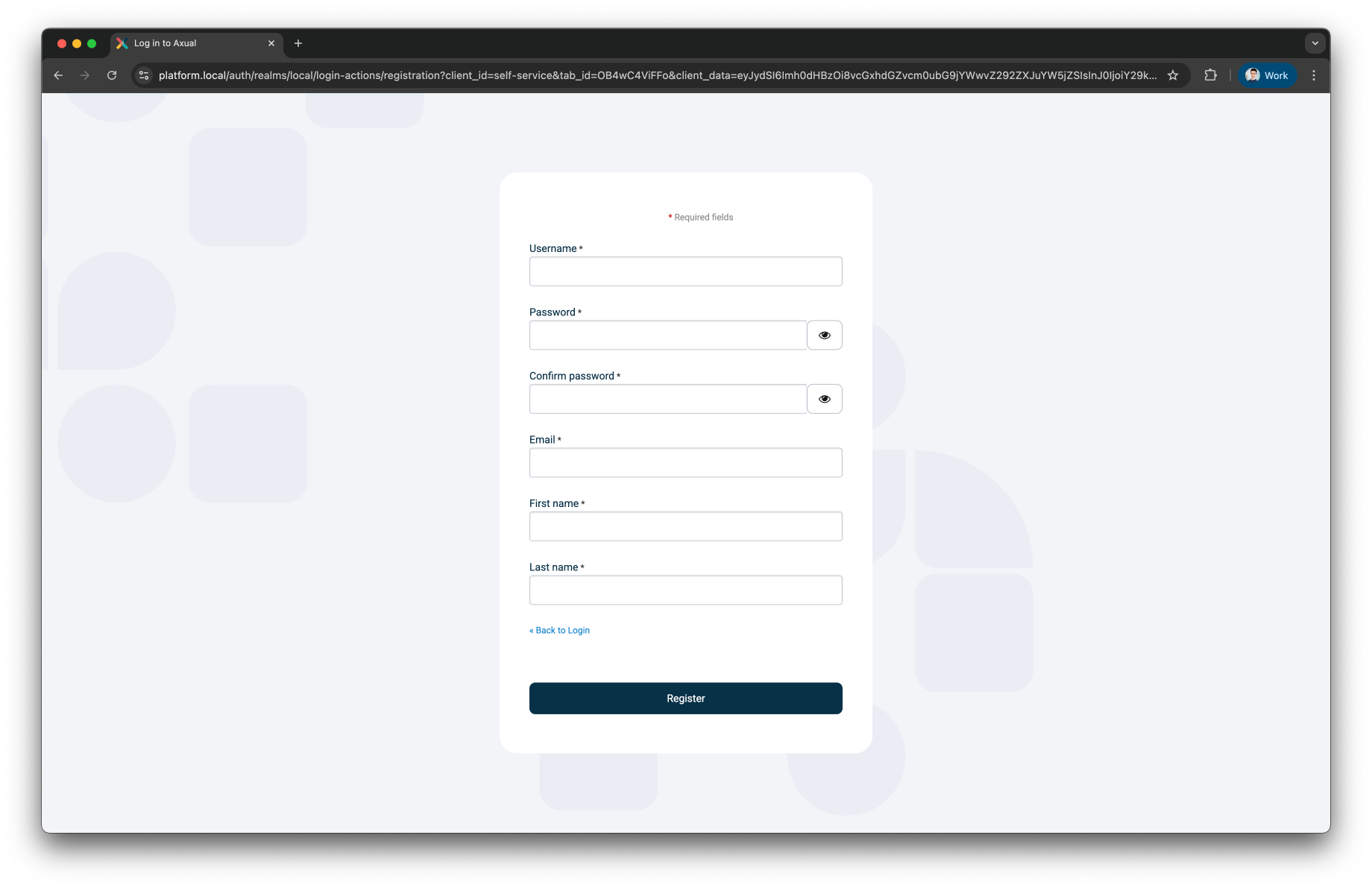
-
Register the tenant admin on your platform. Enter details for the following fields
-
First name
-
Last name
-
Email
-
Username → you will use this to log in next time
-
Password
-
Confirm password
-
-
Click Register to add the user, the following screen will be shown.
-
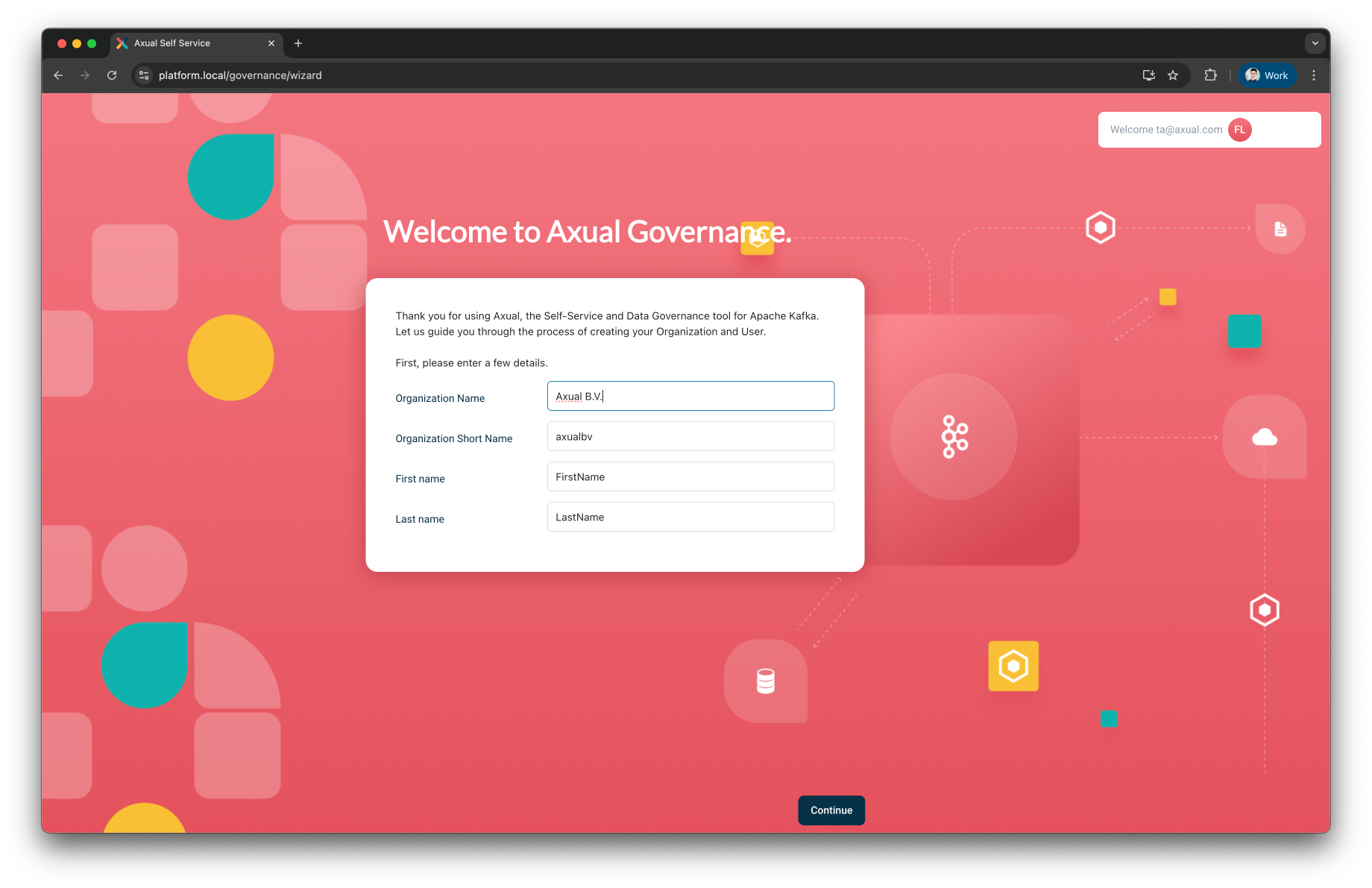
After providing your organization details, click Continue to begin the Kafka cluster onboarding process.
| Tenant Shortname cannot be modified/updated after tenant creation |
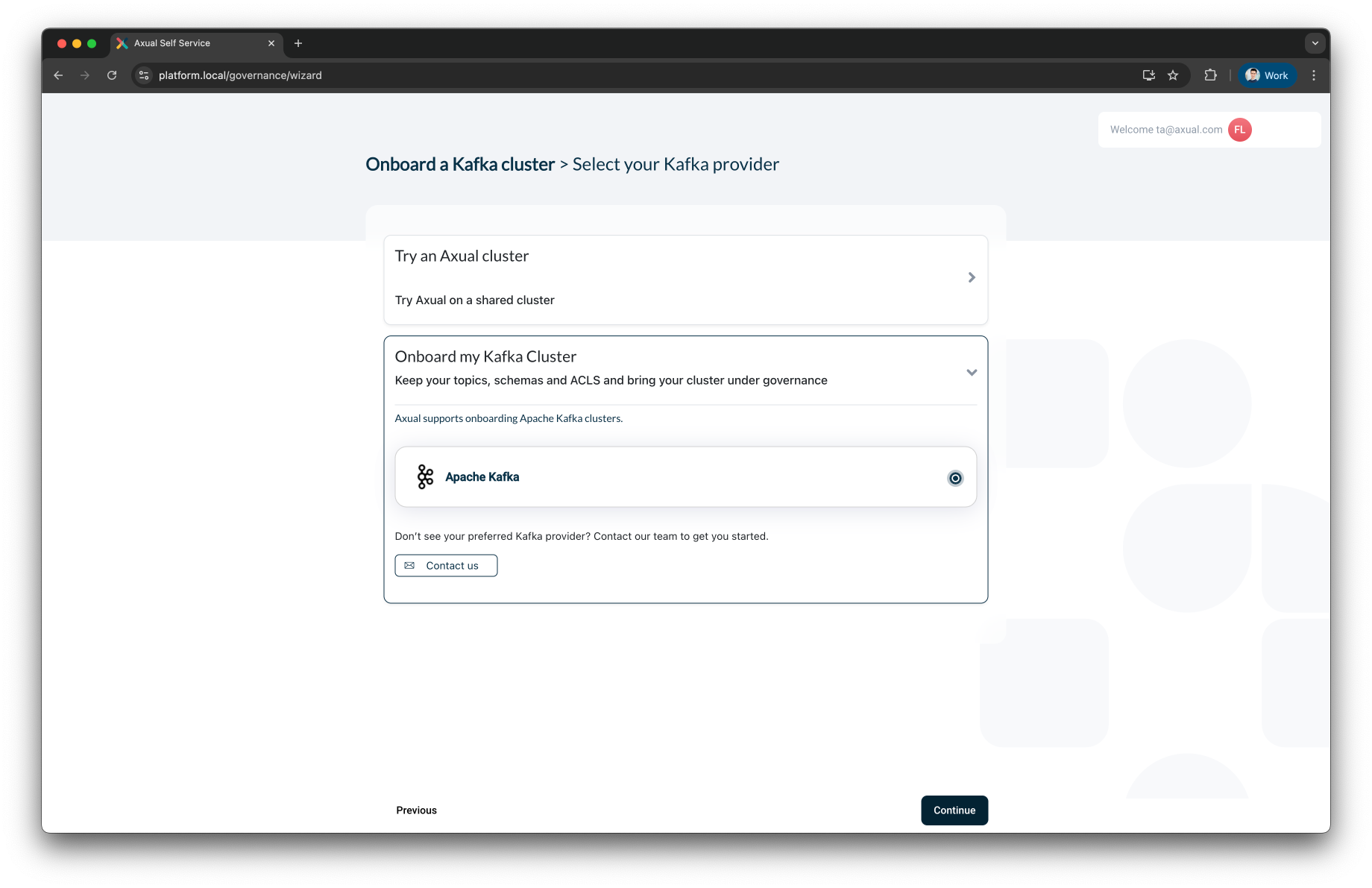
Step 1: Select Your Kafka Provider
You will be presented with options to select a Kafka provider. Onboard my Kafka Cluster – for connecting your own Kafka cluster into Axual governance
-
Select Apache Kafka under "Onboard my Kafka Cluster".
-
Click Continue to proceed to the next step.
Step 2: Enter Your Kafka Cluster Details
Fill in the required Kafka connection fields.
Common Fields (Required for all authentication methods)
-
Kafka bootstrap URL: Provide your Kafka broker in the format
host:port -
Publicly Trusted CA:
-
Enable it if your Kafka cluster uses a certificate signed by a trusted public certificate authority.
-
Disable it if your Kafka cluster uses a custom or private CA.
-
-
Authentication method: Select one of the supported authentication options:
TLSorSASL
Two authentication flows are supported:
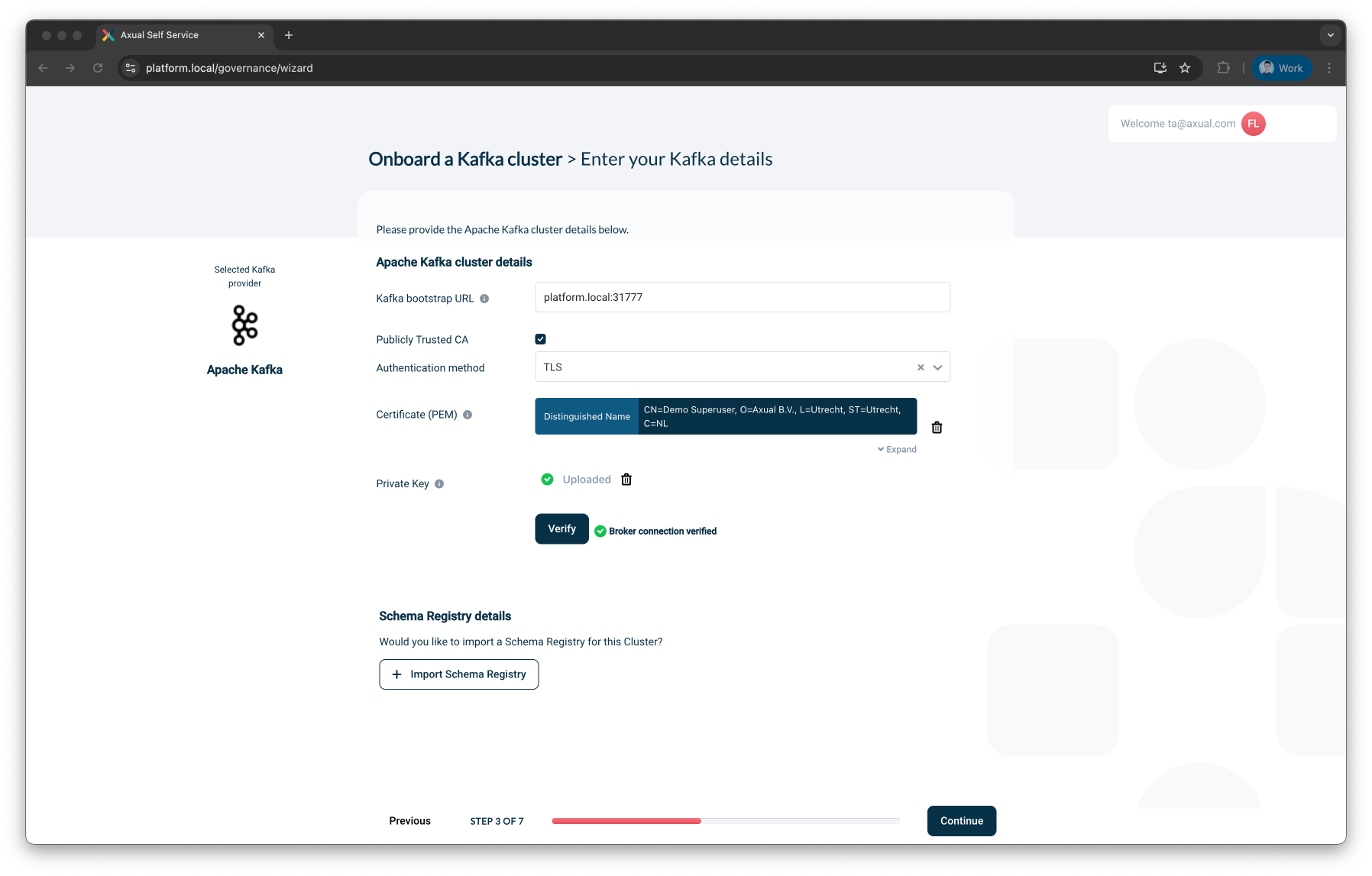
Option 1: TLS Authentication
Use this method when mutual TLS is used for Kafka client authentication.
-
Select
TLSfrom the Authentication method dropdown -
Provide:
-
Certificate (PEM) – Upload the PEM-encoded client certificates. Must be
X.509formatted and should contain the whole certification chain -
Private Key (PEM) – Upload the matching PEM-encoded private key. Must be
pkcs8formatted
-
-
Click Verify to validate the TLS credentials
-
Once verified, click Continue
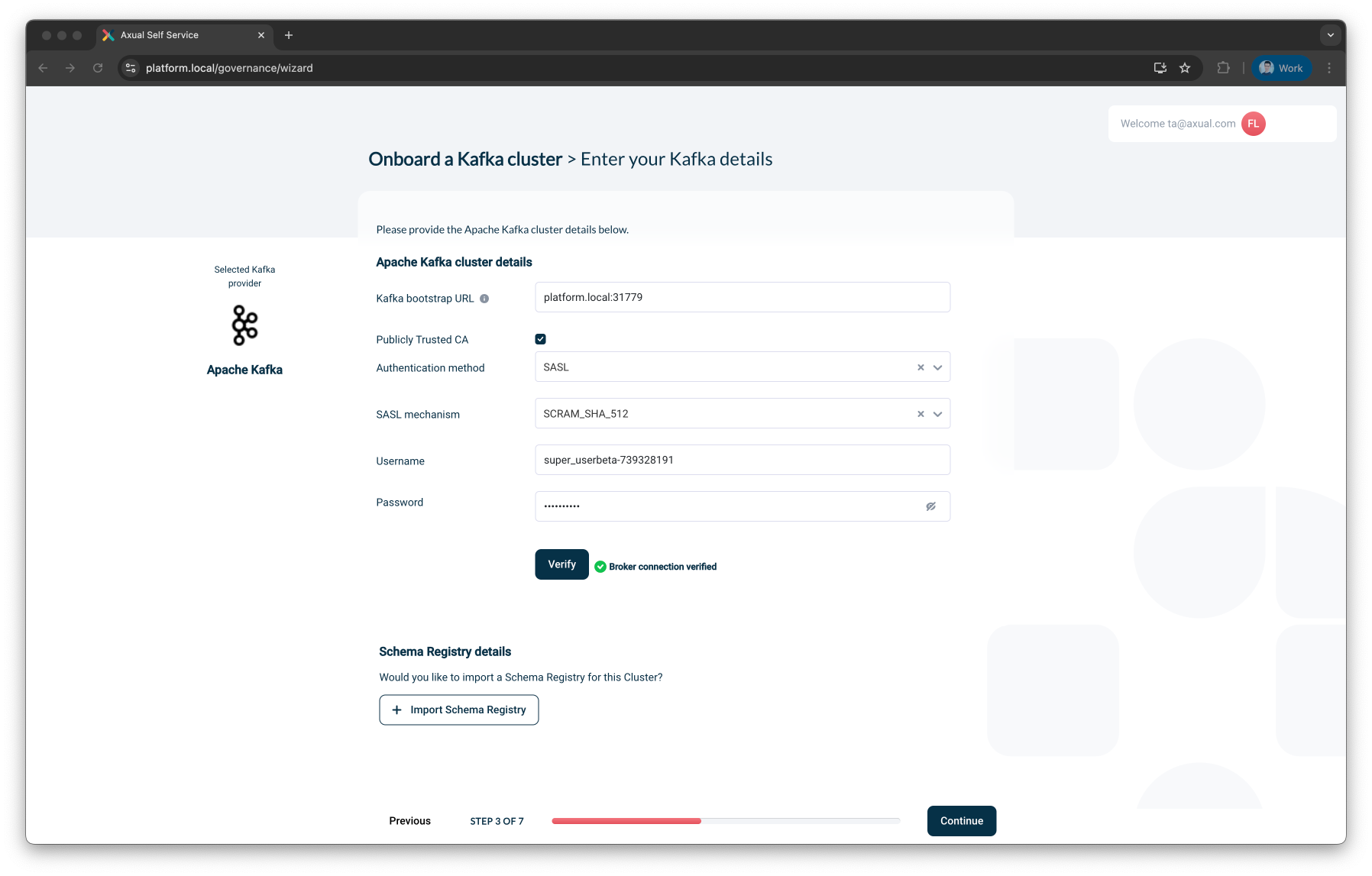
Option 2: SASL Authentication
Use this method if your Kafka cluster uses username/password-based authentication.
-
Select
SASLfrom the Authentication method dropdown -
Select a SASL Mechanism:
-
PLAIN -
SCRAM-SHA-256 -
SCRAM-SHA-512
-
-
Enter the Username
-
Enter the Password
-
Click Verify to validate the SASL credentials
-
Once verified, click Continue
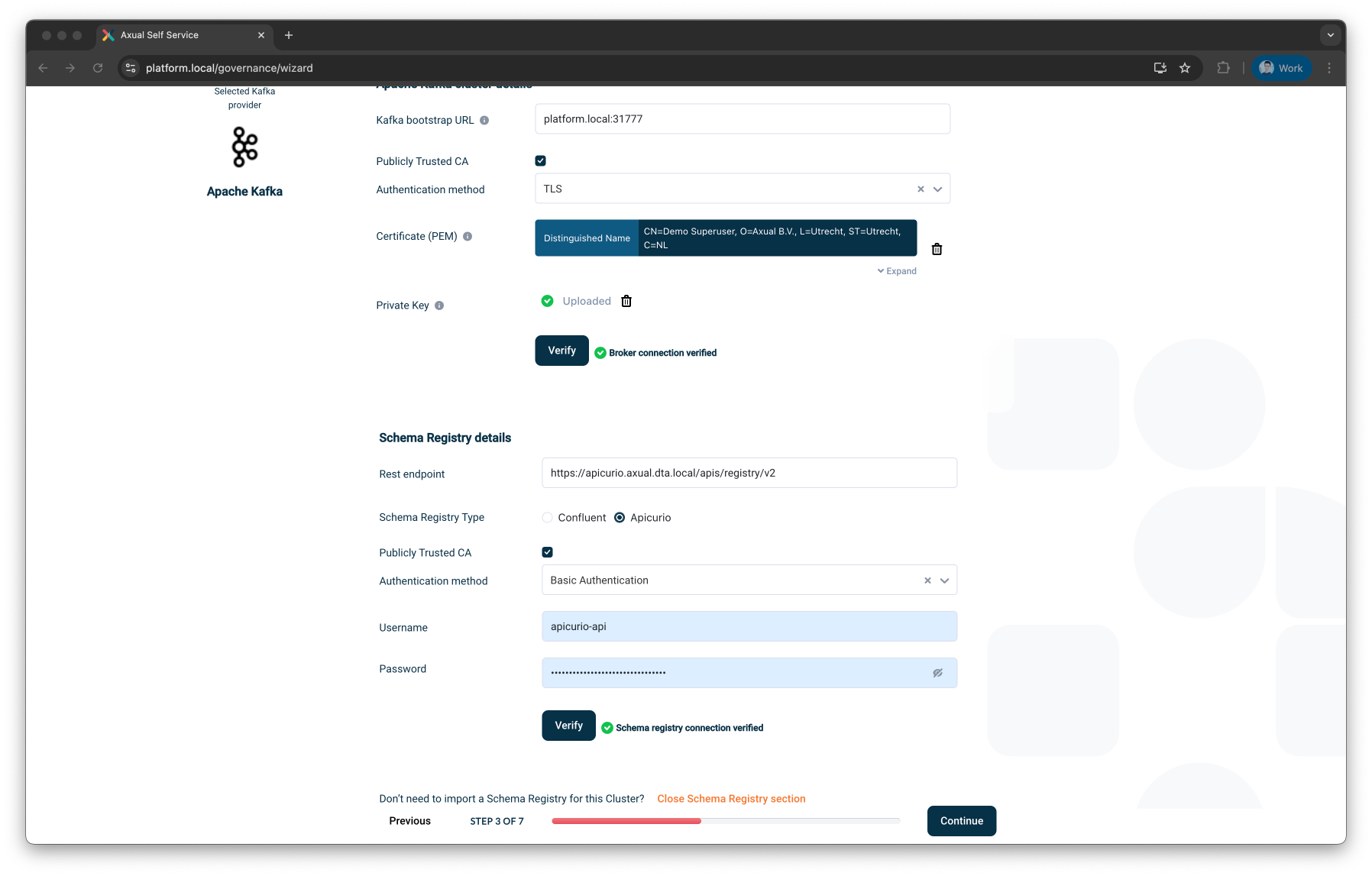
Step 3: Import Schema Registry (Optional)
If your setup includes a Schema Registry, click Import Schema Registry.
Provide the following:
-
REST Endpoint – e.g.
http://my-schema-registry-host:20000 -
Schema Registry Type – Choose between:
-
Confluent -
Apicurio
-
-
Publicly Trusted CA – Allow providing a private signing CA
-
Authentication method – Choose one:
-
No Authentication -
Basic Authentication— Requires username and password -
TLS— Requires a client certificate and private key (PEM)
-
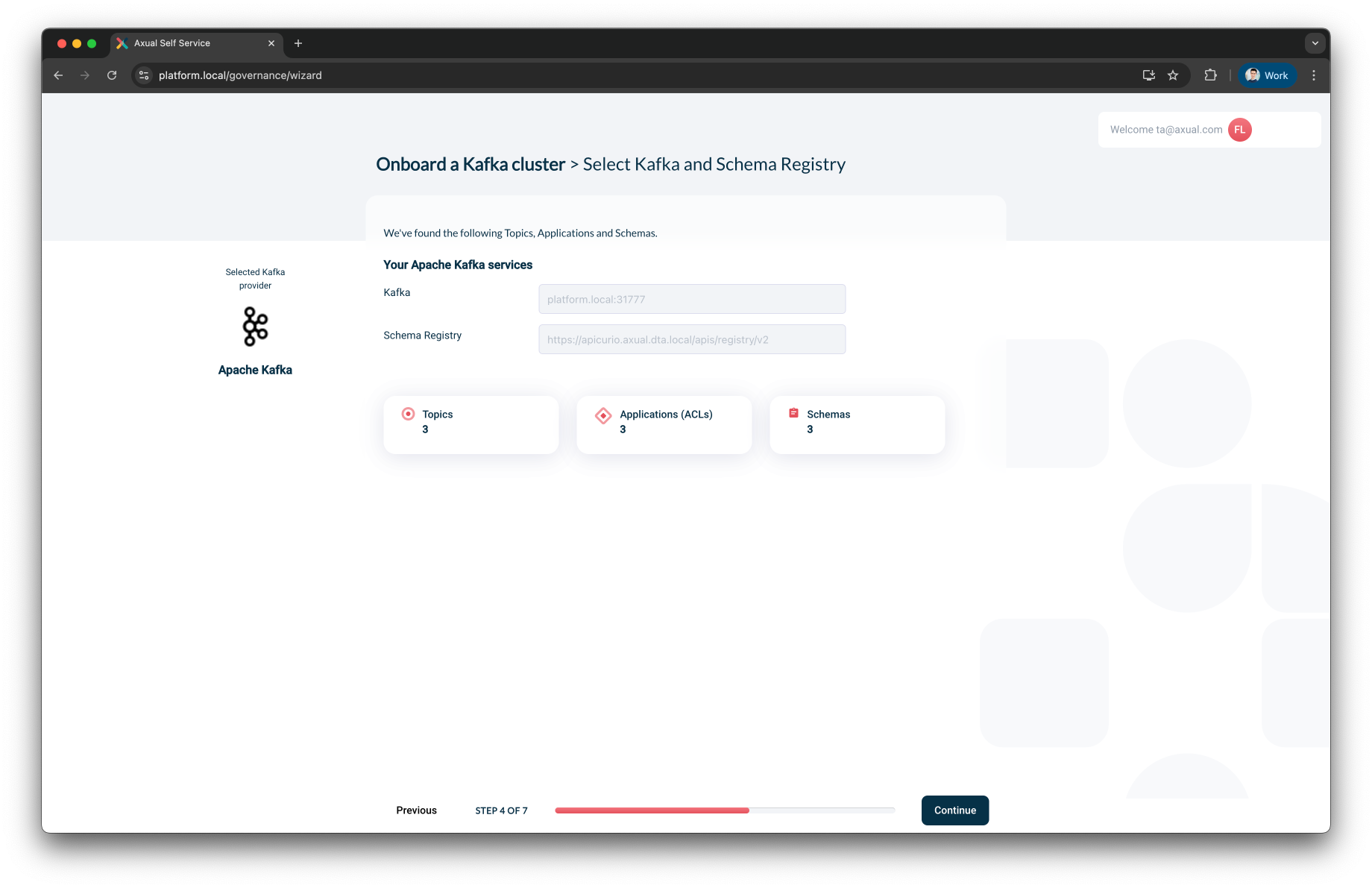
Step 4: Kafka and Schema Discovery
After verifying your Kafka credentials, Axual performs an automatic discovery scan.
The following assets will be detected (if present):
-
Topics
-
Applications (Based on literal ACLs on the imported cluster)
-
Schemas
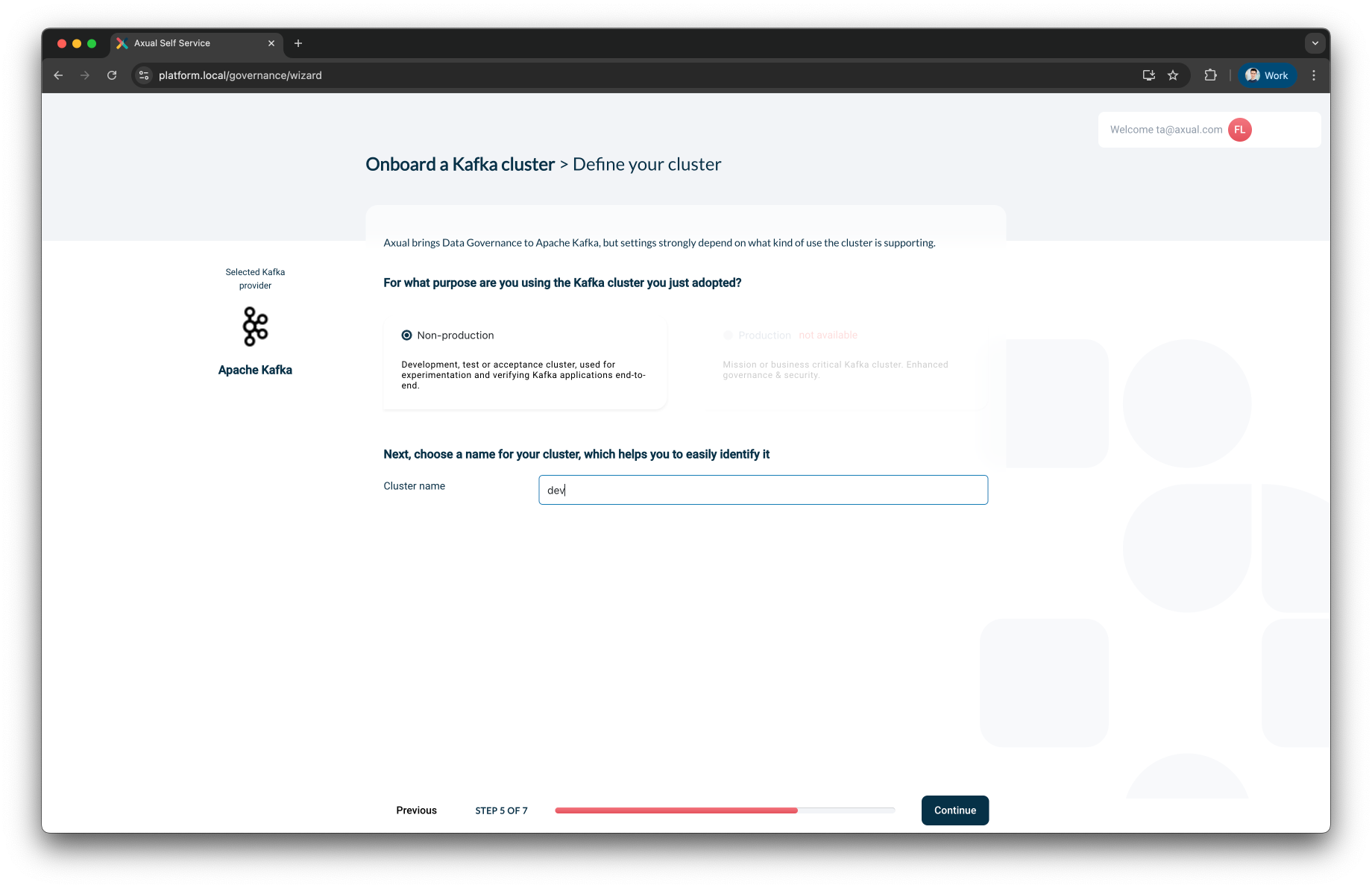
Step 5: Define the Cluster
Define how this cluster will be used:
-
Usage type – Select one:
-
Non-production— for dev/test/staging -
Production— for critical workloads
-
-
Cluster name – Provide a unique, human-readable name for your cluster
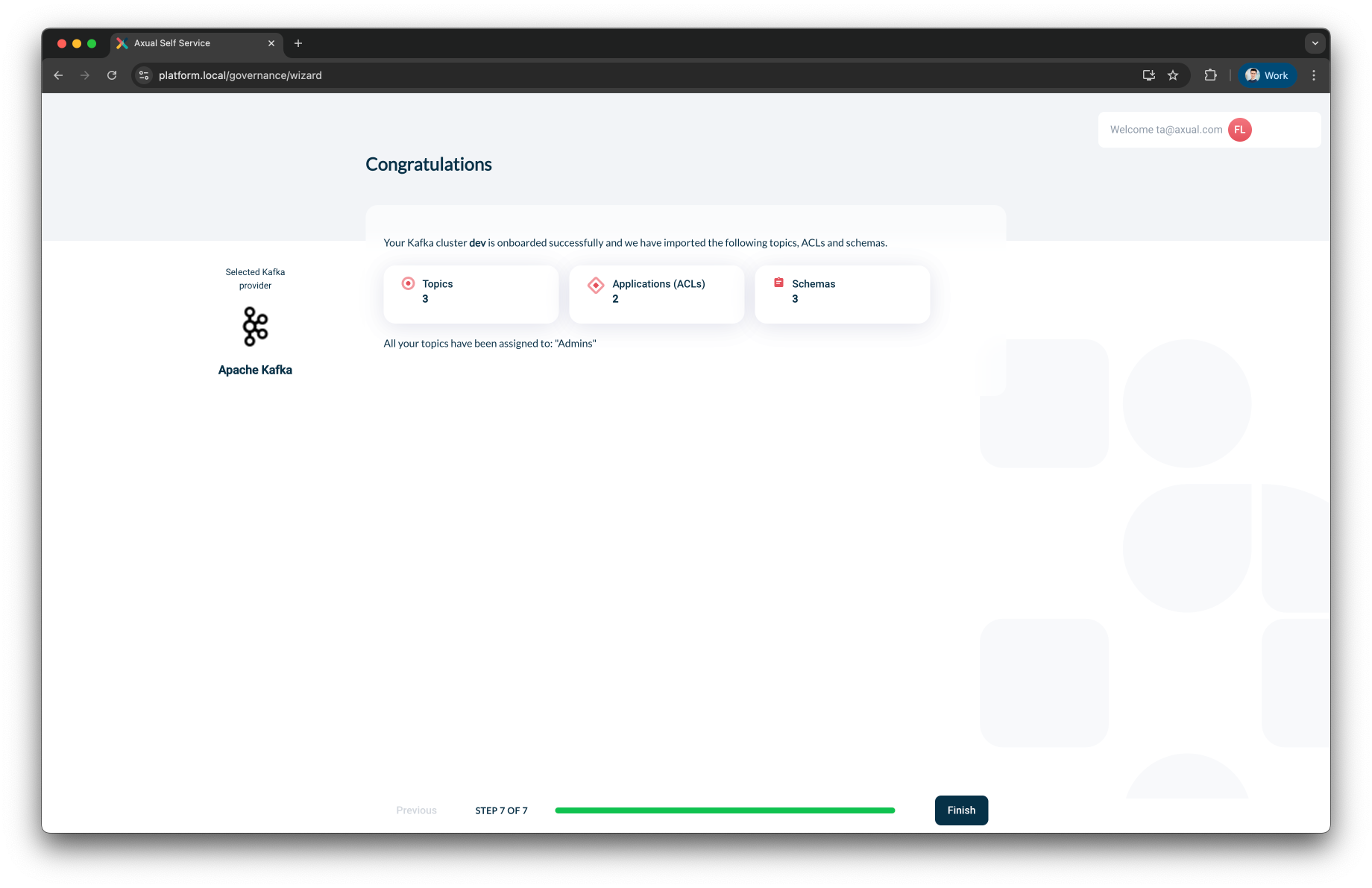
Step 6: Import Existing Topics
Before completing the onboarding process, you will be presented with a summary of actions that Axual will perform.
You will also be able to inspect discovered topics.
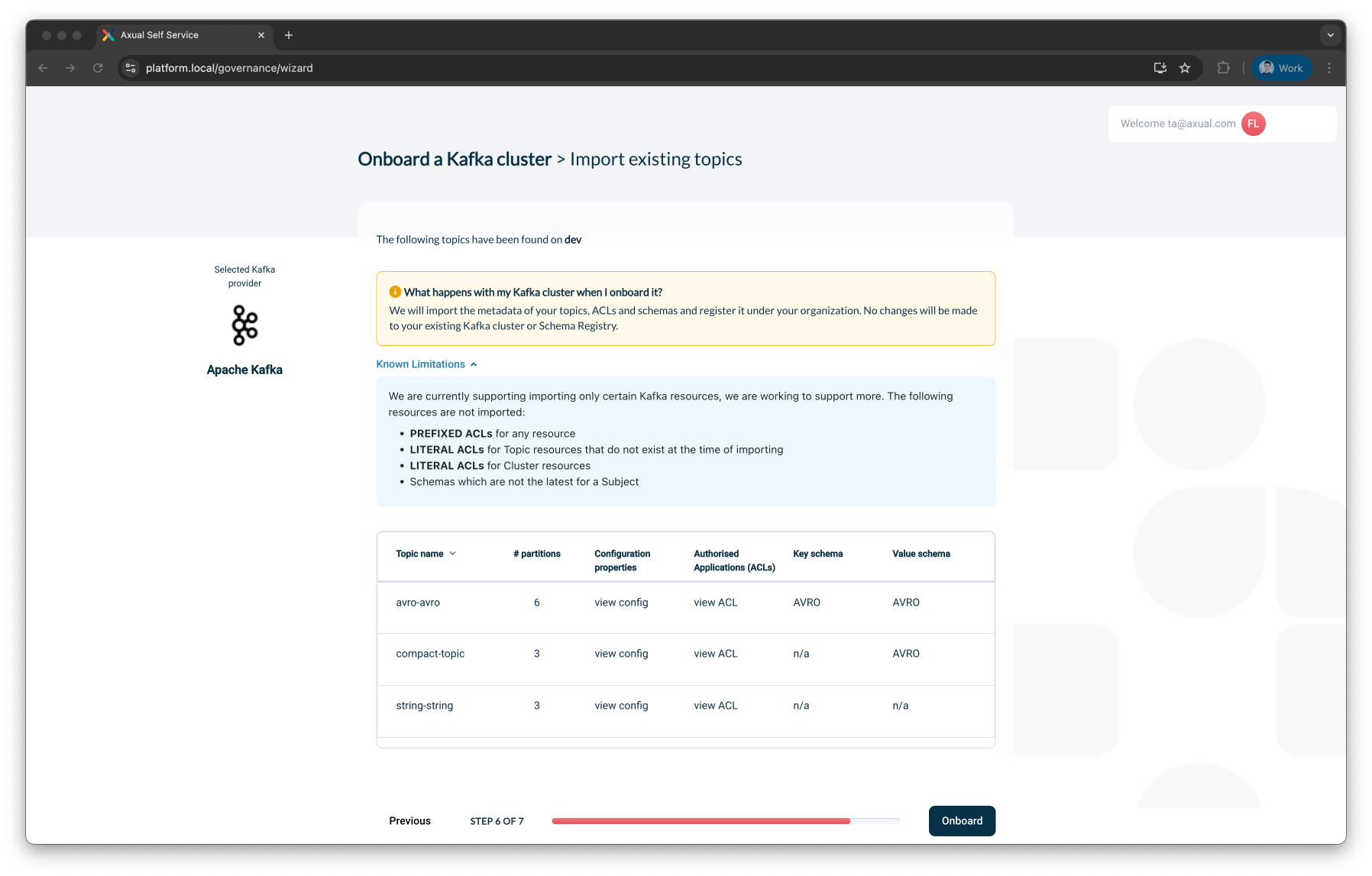
For each discovered topic, you can:
-
Review configuration properties like:
-
Retention policy
-
Cleanup policy
-
Compression type
-
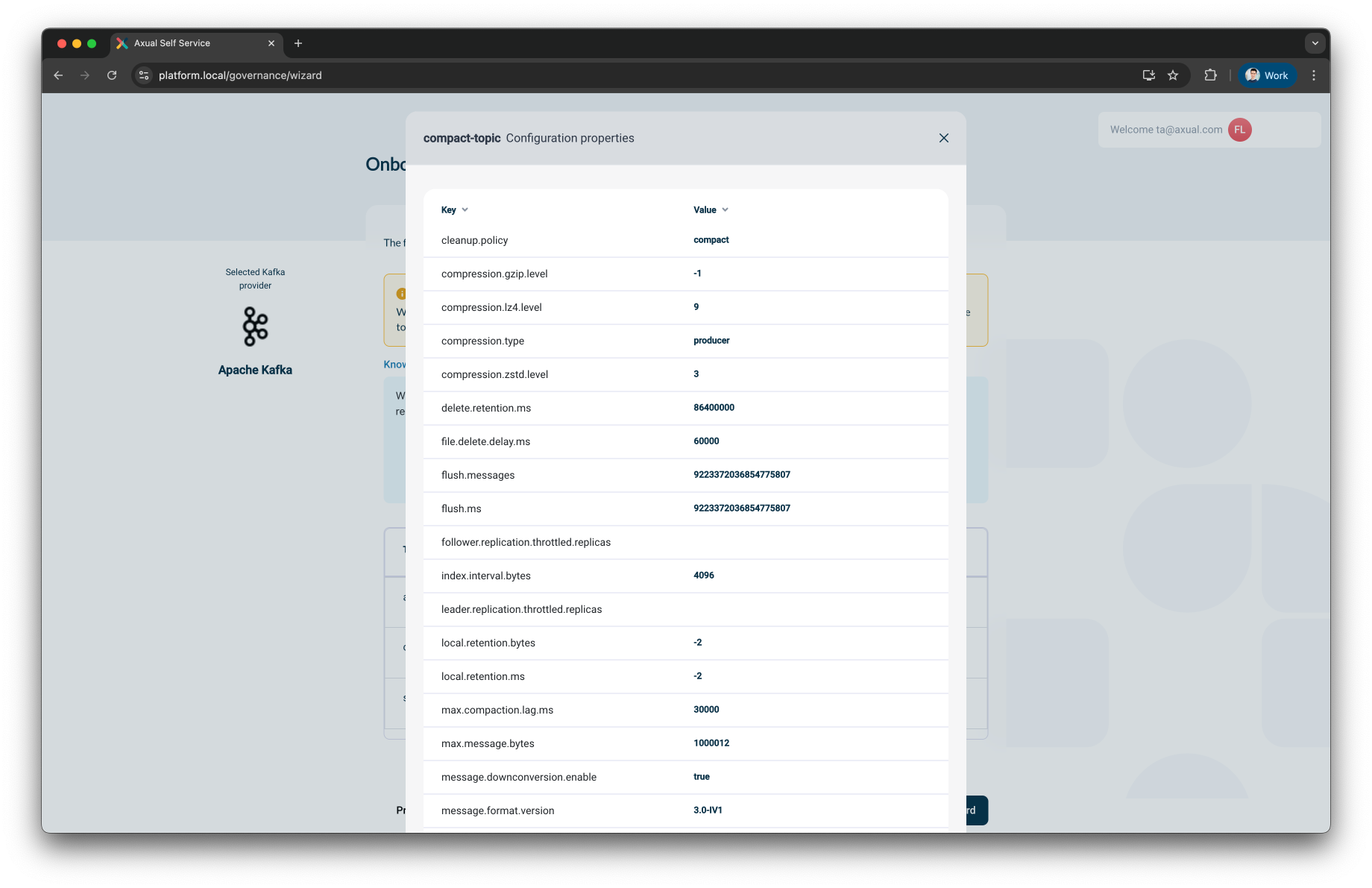
-
Review authorized applications (ACLs):
-
View roles (e.g., producer, consumer)
-
Link to known applications in your governance system
-
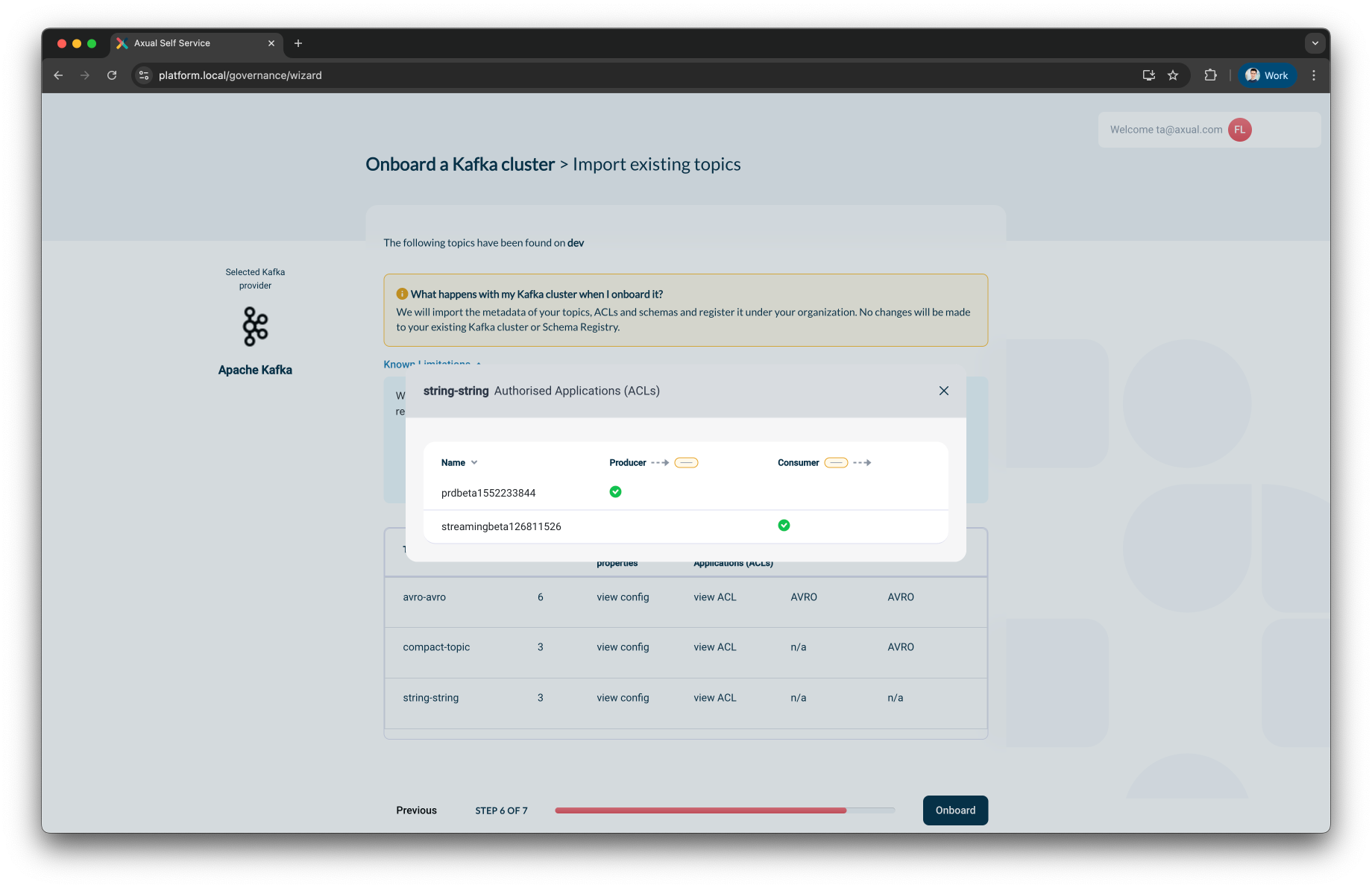
What does Axual do during onboarding?
Axual performs a read-only import of your Kafka cluster metadata. Specifically, it will:
-
Discover and import:
-
Topic configurations
-
Access Control Lists (ACLs)
-
Schema definitions (latest versions only)
-
-
Register these assets into your organization’s governance workspace within Axual
|
Axual does not make any changes to your Kafka cluster, its topics, or your Schema Registry. The process is entirely non-intrusive and read-only. |
Known Limitations
Please be aware of the current limitations of the onboarding process:
-
ACLs defined with a prefixed pattern are not imported
-
ACLs for topics that don’t yet exist are ignored
-
ACLs that apply to Kafka Cluster resources are not imported
-
Only the latest version of each schema subject is imported