Organization Manager 0.3.2 Readme
Overview
The Organization Management component manages organizations (tenants) for the Axual Self-service platform.
It is a stateless component that handles user signups, user invites and SSO integration of the organization with either Auth0 or Keycloak.
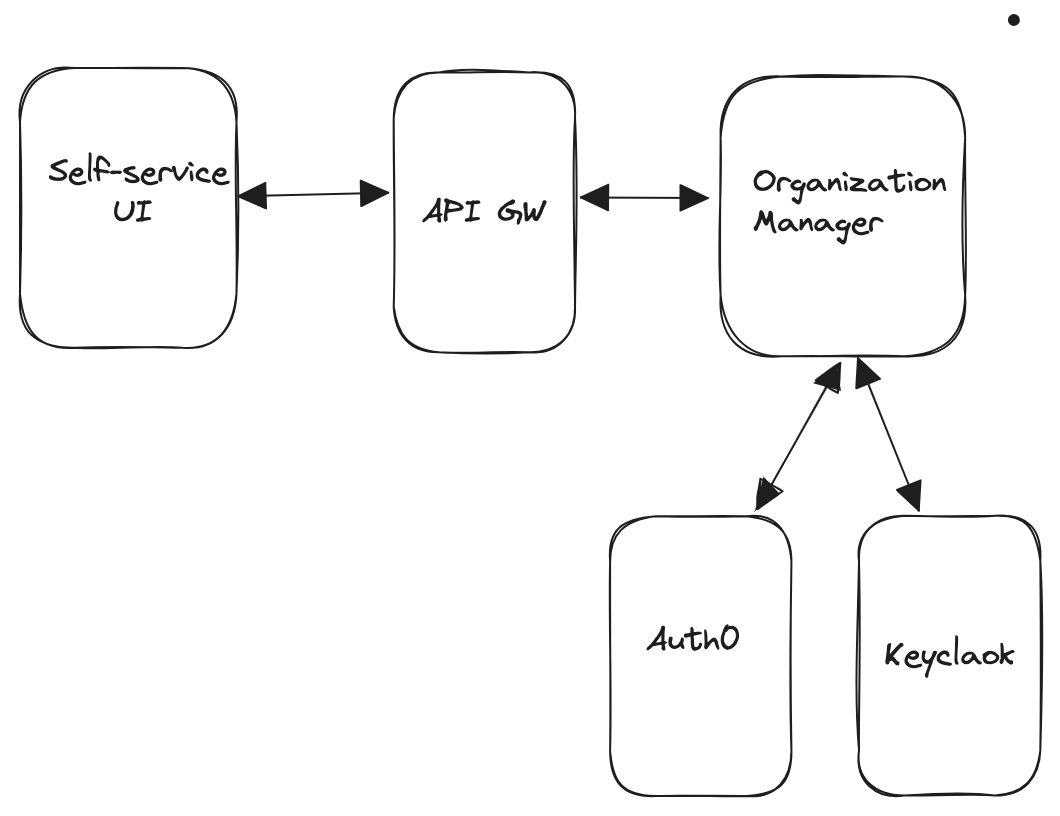
How to Run a Local Environment
1. Using Auth0 as Authentication Server
Get Auth0 Environment Variables
-
Open Applications > APIs
-
Create a new API named
Organization Management API -
Provide an Identifier (should end with the domain of where it’s supposed to run e.g org.mgmt.byok.np.axual.cloud)
-
-
Open Applications > APIs >
Auth0 Management API-
Goto
Machine to Machine Applicationstab -
Authorize the created
Organization Management API
-
-
Open the drop-down beside the
Authorizedswitch/button -
Assign permissions
-
create:users
-
read:users
-
update:users
-
delete:users
-
create:users_app_metadata
-
read:users_app_metadata
-
update:users_app_metadata
-
delete:users_app_metadata
-
-
Press
Updatebutton to save the permissions -
Go to the Auth0 portal and use the
Auth0 Management APIidentifier as youraudience -
Goto
Organization Management API (Test)from theApplicationsmenu -
In the
Settingstab, copy thedomain,clientIdandclientSecretvalues and paste in the corresponding env variables
Provide the following values as config
{
"authStrategy": "auth0"
"auth0Domain": "{auth0 domain registered in auth0 portal for the API application in Applications}"
"auth0ClientId": "{auth0 client ID registered for the API application in Applications}"
"auth0ClientSecret": "{auth0 client secret registered for the API application in Applications}"
"auth0Audience": "{auth0 API audience of the Auth0 Management API in auth0 portal}"
"auth0DatabaseName": "{auth0 name of the db connection in auth0 portal}"
}
| Name | Possible Values | Required | Description |
|---|---|---|---|
authStrategy |
|
True |
the authentication provider for the installation |
auth0Domain |
string |
True |
domain registered in the auth0 portal for the application |
auth0ClientId |
string |
True |
client ID registered for the application in auth0 portal |
auth0ClientSecret |
string |
True |
client secret registered for the application in auth0 portal |
auth0Audience |
string |
True |
API audience of the Auth0 Management API in the portal |
auth0DatabaseName |
string |
True |
name of the db connection in auth0 portal |
2. Using Keycloak as Authentication Server
Get Keycloak Environment Variables
-
Go to the Keycloak portal and login
-
Note your login
usernameandpasswordaskeycloakCLIUsernameandkeycloakCLIPasswordrespectively -
Paste your
keycloakDomain,keycloakCLIUsernameandkeycloakCLIPasswordin the corresponding env variables
Provide the following values as config
{
"authStrategy": "keycloak"
"keycloakDomain": "{full https keycloak domain registered in keycloak portal}"
"keycloakCLIUsername": "{keycloak admin-cli username that is used to login into the admin console}"
"keycloakCLIPassword": "{keycloak password that is used to login into the admin console}"
"tlsVerification": "{toggle tls veriification}"
"trustStore":"{path to the CA certificate file for validating `tls`}"
}
| Name | Possible Values | Required | Description |
|---|---|---|---|
authStrategy |
|
True |
the authentication provider for the installation |
keycloakDomain |
string |
True |
full https keycloak domain registered in keycloak portal |
keycloakCLIUsername |
string |
True |
keycloak admin-cli username that is used to login into the admin console |
keycloakCLIPassword |
string |
True |
keycloak password that is used to login into the admin console |
tlsVerification |
boolean |
False. Defaults to |
Toggle |
trustStore |
string |
False |
path to the CA certificate file for
validating |