Security
Securing Your Streaming Use Case
When building your streaming use case, you might be dealing with sensitive information: data that should not end up in the wrong hands. For this reason, security is an essential aspect of Axual and enabled by default.
-
Data is encrypted in-flight, between the client and the platform
-
Clients are authenticated and authorized against every stream-deployment
Axual supports 2 Authentication Methods: Simple Authentication & Security Layer (SASL) and Mutual TLS (SSL).
Simple Authentication and Security Layer (SASL)
Simple Authentication and Security Layer is a framework for authentication and data security in Internet protocols.
-
With SASL
SCRAM_SHA, you can easily authenticate your applications by providing the username/password combination generated in the Platform Manager portal. -
With SASL
OAUTH_BEARER, you can authenticate your applications by providing a clientId registered in your IAM Provider.
Mutual TLS: The Foundation
Mutual Transport Layer Security (mTLS) is a process that ensures two parties can communicate securely over an insecure medium, as well as authenticate (identify) each other. A requirement for this process to take place is sharing digital certificates ahead of time.
1. Setting Up Trust
A truststore is used to set up trust between the platform and producing or consuming clients. The truststore contains the certificate of the Certificate Authority (abbreviated as "CA") and potentially any intermediate certificates which sign application certificates.
During the handshake between client and server, the server will present its certificate, which the client needs to trust before establishing a secure connection. This happens regardless of the authentication mechanism. When authenticating via mTLS, the client will also present a certificate which the server must trust ahead of time.
If using the Axual-Trial, you will find the truststore in the root directory of the care package, which has been sent to you when your trial was ready:
-
[yourcompany]xxxx.truststore.jks: the truststore, used by Java clients -
[yourcompany]xxxx-root-ca.cert.pem: the ROOT CA file used by REST Proxy and .NET clients
2. Application Certificate
Next, you need a certificate for your consumer/producer, which is issued by the CA or the intermediate CA.
If using the Axual-Trial, you will find some certificates you can use in your applications in the care package directory named [yourcompany]xxxx-app-keystores:
-
[yourcompany]xxxx-application-one.cert.pem: the application certificate PEM file -
[yourcompany]xxxx-application-one.key.pem: the application private key PEM file -
[yourcompany]xxxx-application-one.keystore.jks: the application keystore -
[yourcompany]xxxx-application-one.p12: the application p12 file
|
Not using Axual Trial?
If you are not using the Axual Trial (i.e. Axual-Cloud or an on-premises installation), the truststore and application certificates you need depend on your company’s Public Key Infrastructure (PKI). In this case, get in touch with your company’s Streaming Team and make sure you use the truststore they advise and request a certificate signed by the appropriate authority. |
The application principal is used to authorize the application to use the stream (either producing or consuming). The principal is formed by the Distinguished Name (DN) of the certificate used by the application.
To configure the application principal on the selected environment:
-
Visit the detail page of the application.
-
Select the "example" environment for which we want to configure the principal
-
Click on the Padlock button in the application box (hovering over it will show the text 'Authentication'). You will see a modal as below:
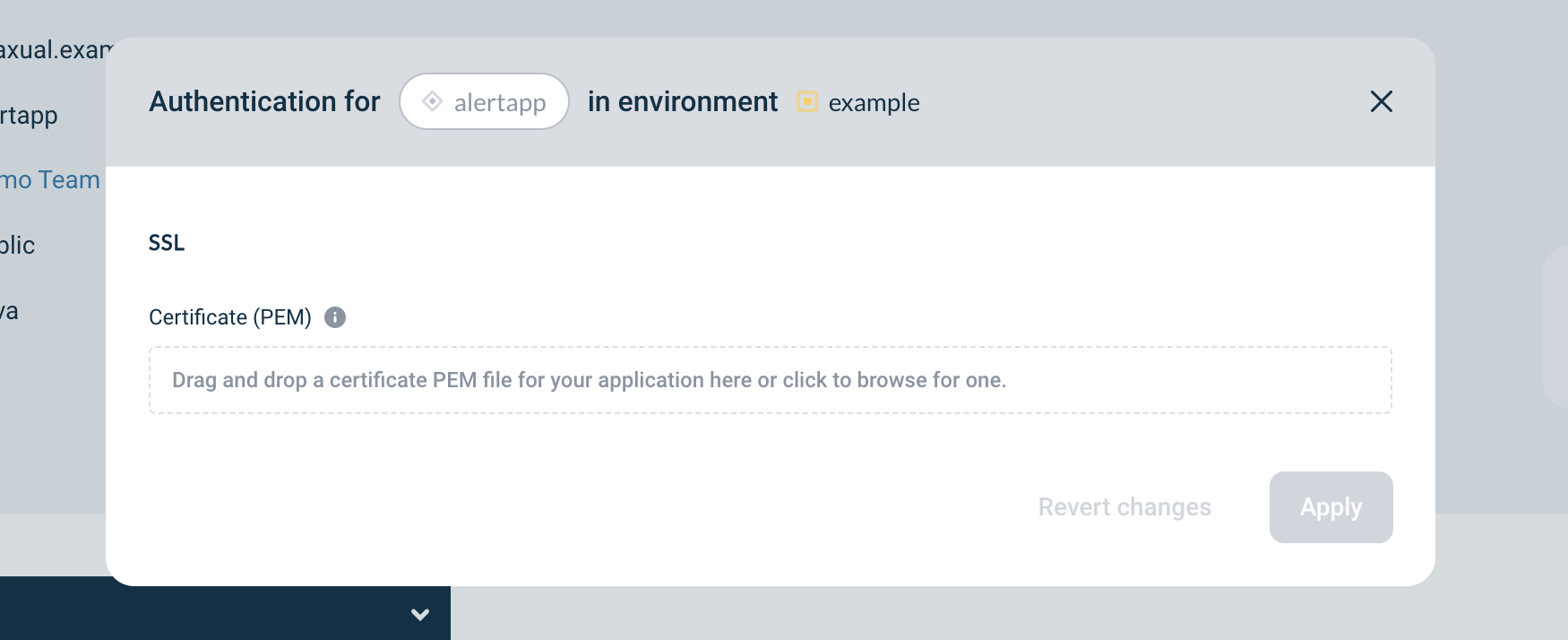
-
Upload your application certificate.
The certificate file for your Getting Started application can be found in your care package. See also 2 Application Certificate -
The certificate chain will be shown. Confirm that the uploaded certificate matches the certificate you will use for your application in the corresponding environment.
-
Click on Apply.
The application box name will turn green indicating that the application is configured properly on that environment. Above steps can be repeated for different environments where application is required to access the stream.
Repeat the steps above for your Consumer application.
| Check this page to learn how to generate a PEM file from the keystore which stores your certificate. |