Common operations
This doc provides steps to create a CI/CD user for common operations with Axual Platform.
Already have CI/CD User?
Please follow Use CI/CD user for integrate the API with the CI/CD user.
Identify necessary endpoints
Check which endpoints to use by looking at the information below.
| Service | Endpoint | Purpose |
|---|---|---|
Management API |
"https://<MGMT_DOMAIN>/api" |
Resource Server for creating streams, applications and more resource |
Keycloak Token |
"https://<MGMT_KEYCLOAK_DOMAIN>/auth/realms/<your-realm>/protocol/openid-connect/token" |
Authorization Server for obtaining JWT token |
In case you are not using any load-balancer, use the MGMT_API_HOST:MGMT_API_PORT and KEYCLOAK_HOSTNAME:KEYCLOAK_PORT
|
1. Create CI/CD User
Management API is a protected OAuth2 Resource Server. You need a valid JWT token to successfully interact with the Management API. The token can be obtained from the Authorization Server which is Keycloak. For this, a client registration must be done.
The flow is Resource Owner Password Credentials.
Required information to create a CI/CD user
Before moving forward, identify
-
Realm for which the CI/CD user is needed
-
CI/CD user first_name, last_name, and email
Create the CI/CD user in Keycloak
-
Login into Keycloak Admin Console, usually done by port forwarding the Keycloak Admin port in HELM. In case you are using Axual CLI connect by using the KEYCLOAK_ADMIN_PORT.
-
Switch to the correct realm.
-
Click ok Users on the left-side menu.
-
Click on Add user on the right side of the page.
-
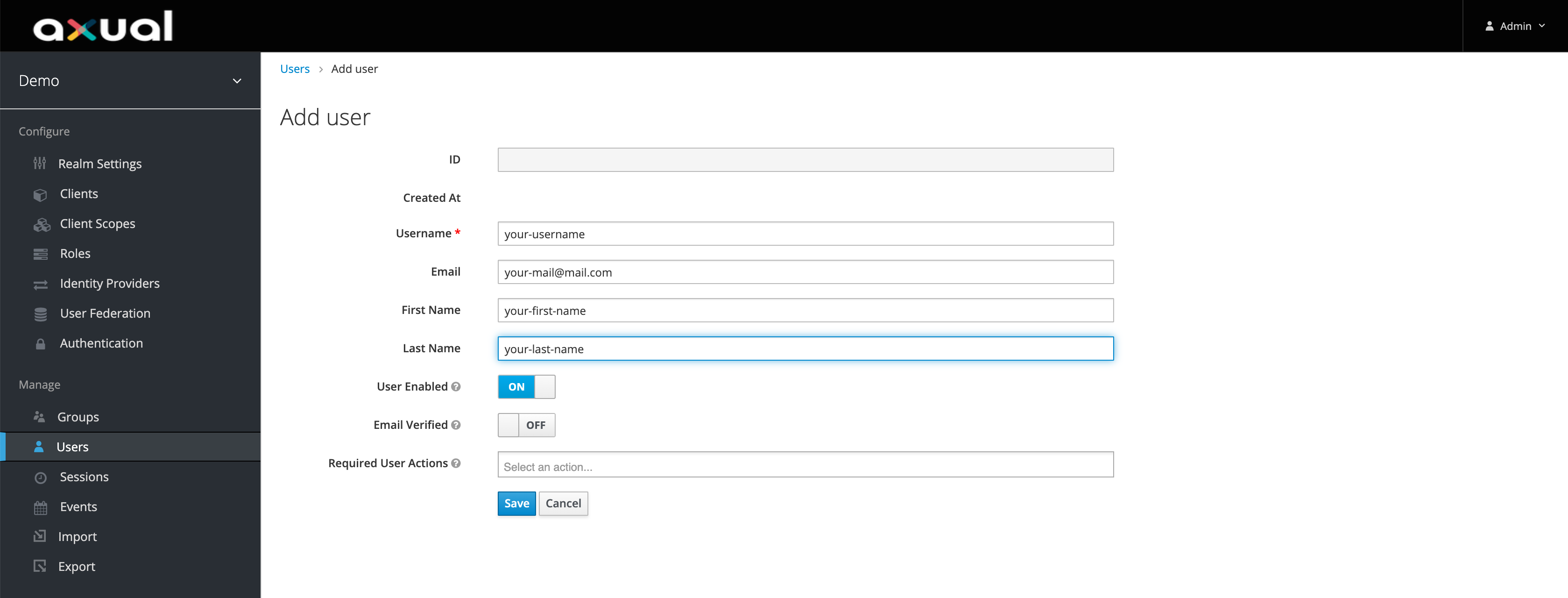
Fill in the user details, make sure first_name, last_name, and email are filled in, else it will fail at later step.
-
Click on Save.
-
Click on Credentials tba and set a decent password.
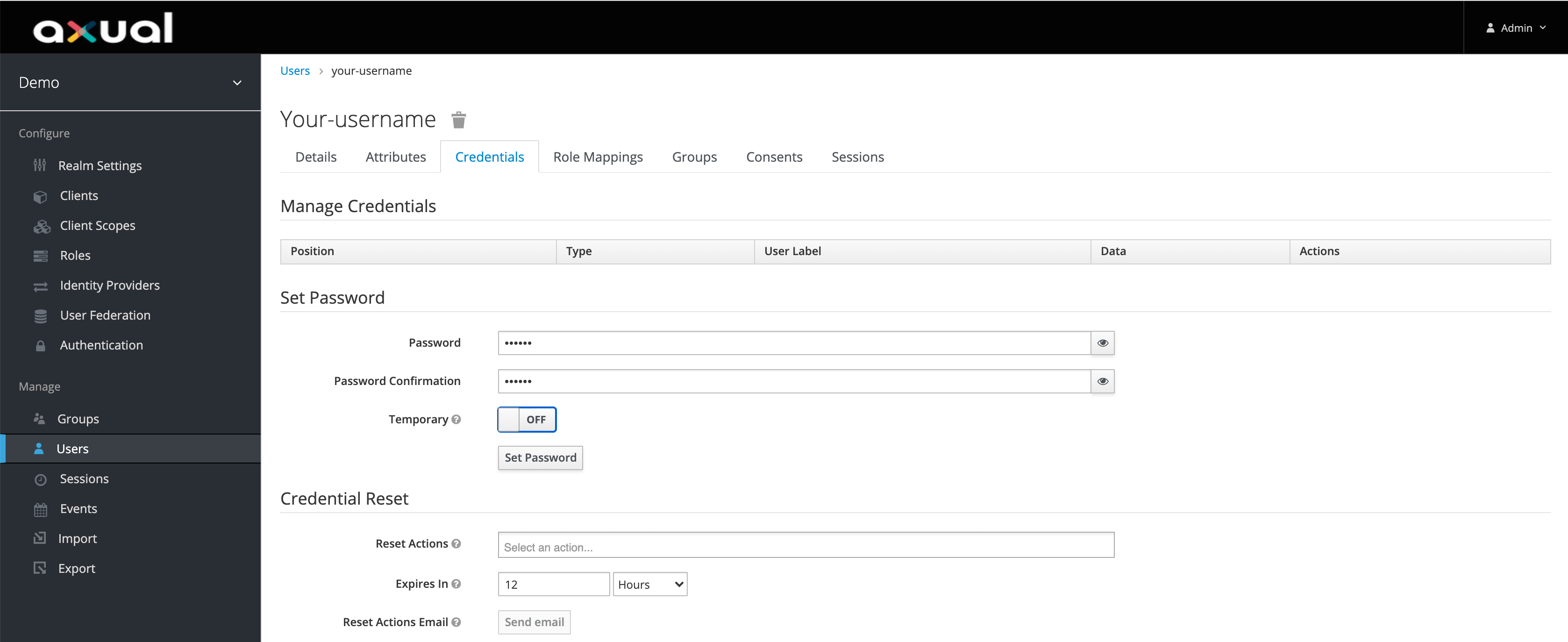
Make sure Temporary is turned off -
Now you have a username and password you can use.
2. Persist the CI/CD user in the Self-Service
Obtain a JWT token
To obtain a JWT token, make a call to the Authorization Server (Keycloak) with client ID, username, password and realm to receive a JWT token.
Below is an example CURL call
curl --request POST \
--url https://<MGMT_KEYCLOAK_DOMAIN>/auth/realms/<your_realm>/protocol/openid-connect/token \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data client_id=self-service \
--data username=<username> \
--data password=<password> \
--data realm=<your_realm> \
--data grant_type=password
If this host is using self-signed certificates or certificates signed by an untrusted certificate authority, you need to add --insecure
|
You should get back a 200 OK response with the access_token (JWT) inside.
{
"access_token": "eyJh...",
"expires_in": 299,
"refresh_expires_in": 3600,
"refresh_token": "zfAu...",
"token_type": "bearer",
"not-before-policy": 0,
"session_state": "899970b8-8058-48da-ae95-7797010f59da",
"scope": "profile email"
}Call Management API with JWT token
With the access_token received in previous request, make a curl call to Management API with the access_token as the Bearer value to /api/user for creating the CI/CD user in the Self-Service.
| This call is required to find the CI/CD user in the Self-Service portal |
Below is an example CURL call to retrieve the logged user information
curl --request GET \
--url 'https:/<MGMT_DOMAIN>/api/user' \
--header 'Authorization: Bearer <access_token>' \
--header 'realm: <your_realm>'
If this host is using self-signed certificates or certificates signed by an untrusted certificate authority, you need to add --insecure
|
You should get back a response like below.
{
"firstName": "<your_ci_cd_name>",
"lastName": "<your_ci_cd_last_name>",
"middleName": null,
"emailAddress": {
"email": "<your_ci_cd_email>"
},
"phoneNumber": null,
"roles": [
{
"name": "ENVIRONMENT_AUTHOR"
},
{
"name": "APPLICATION_AUTHOR"
},
{
"name": "STREAM_AUTHOR"
}
],
"uid": "xyz",
"created_at": "2021-04-17T14:59:31",
"modified_at": "2021-04-17T14:59:31",
"created_by": null,
"modified_by": null,
"_links": {
"self": {
"href": "https://<MGMT_DOMAIN>/api/users/xyz{?projection}",
"templated": true,
"title": "URI pointing to current request"
},
"user": {
"href": "https://<MGMT_DOMAIN>/api/users/xyz{?projection}",
"templated": true,
"title": "A user"
}
}
}| Now you can share the CI/CD credentials with the developer to perform calls to Management API |